Blog
-
Recovery Point Objective & Recovery Time Objective Demystified
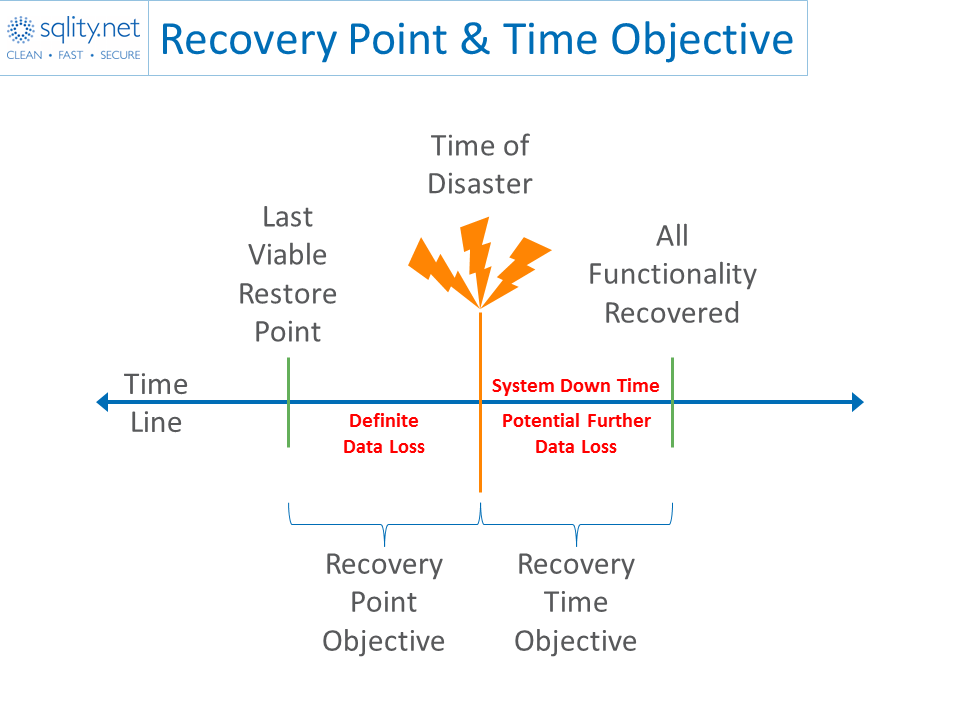
Does you Disaster Recovery Strategy meet your business needs? Learn how to set your Recovery Point Objective and Recovery Time Objective!
-
Five Steps to create an Effective Business Continuity Plan

Disaster can strike at any time. Are you ready? Can your business survive the impact of a disaster? Discover the simple five steps to get a Business Continuity Plan for your business in place today.
-
Fragile Tests – A Ticking Time Bomb

Fragile tests can rob you of the benefits of unit testing by undermining the developer’s trust in the tests. Read on and discover what makes fragile tests so destructive.
-
How to Script Database Permissions
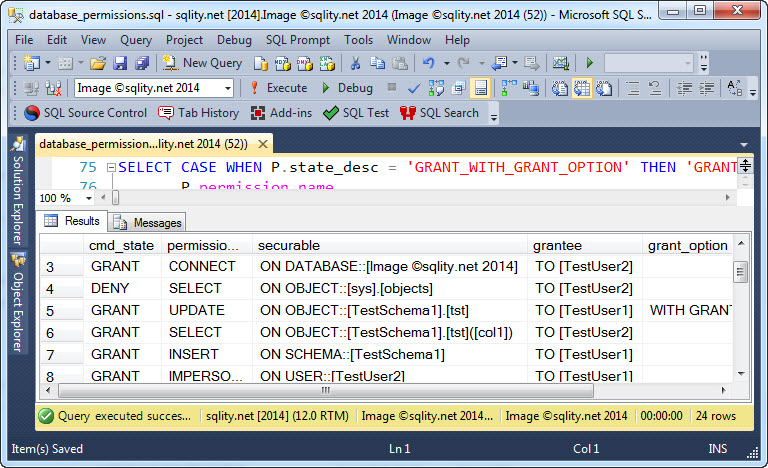
Scripting all permissions in a SQL Server database is not trivial. Discover how to generate the necessary statements yourself with this simple query. (Well, copy & paste of the query is simple…)
-
Common Database Vulnerabilities: Defects

Defects are a nuisance. However, they often lead to bigger problems. You might find your code corruption data by updating the wrong records or opening up gaping security holes allowing users to see other users’ data. Find out how to protect yourself from this danger.
-
Common Database Vulnerabilities: Data Inference

Data inference allows attackers to infer protected information from legitimately accessible data. Read on to find out what data inference entails and how you can protect your data.
-
Common Database Vulnerabilities: Weak Audit Trail

A weak audit trail makes a post-breach-investigation hard. Discover how an effective strategy can act as a deterrent and might be a regulatory requirement.
-
Common Database Vulnerabilities: Flawed Key Management

Encrypting important data is not enough. You also need to handle the encryption keys correctly. Read on to see what flawed key management can result in.
-
T-SQL Tuesday #58 – Round-Up

Last week was the 58th #tsql2sday party and 11 people showed up. There were exciting discussions about password strength, password management, hashing and more. Read on to see what everyone contributed.
-
Five Ways to Manage your SQL Server Passwords [T-SQL Tuesday #58 – Passwords]

Do you have a large number of SQL Server to manage? Read on to discover five ways to manage all your SA passwords and their unique advantages and disadvantages.












