Blog
-
Partition Boundaries – Left or Right: That is the Question
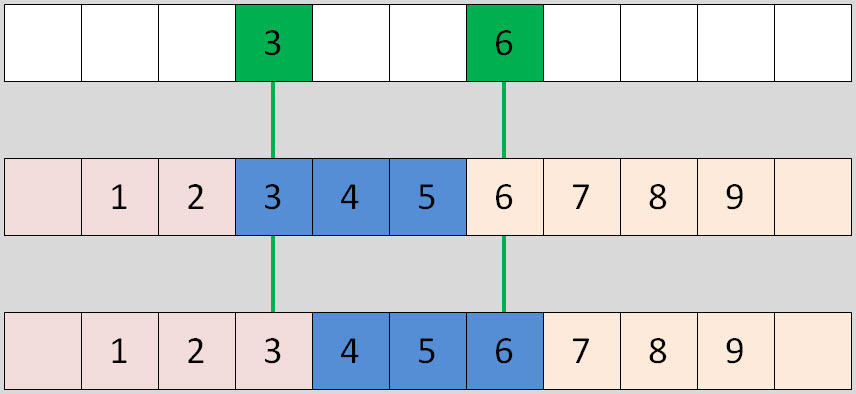
Do you know the difference between a RANGE LEFT and a RANGE RIGHT partition function? Read on and discover a unique query to determine the actual partition a row is stored in. With this query you can quickly confirm your RANGE-assumption or find out where you got it wrong.
-
How to Crack the Symmetric Keys in the Database Wide Open
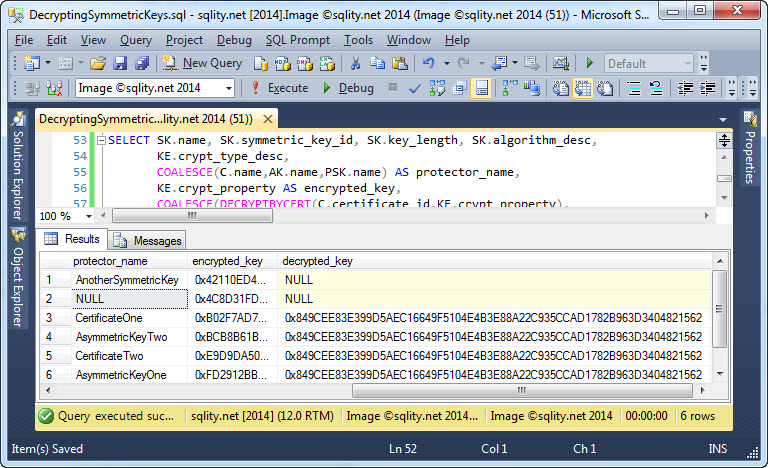
Did you always want to get to the root of symmetric key encryption in SQL Server and actually decrypt a protected symmetric key? In some circumstances this can actually be done. Find out how to do this now.
-
OPEN SYMMETRIC KEY – Avoid the NULL Ciphertext Trap
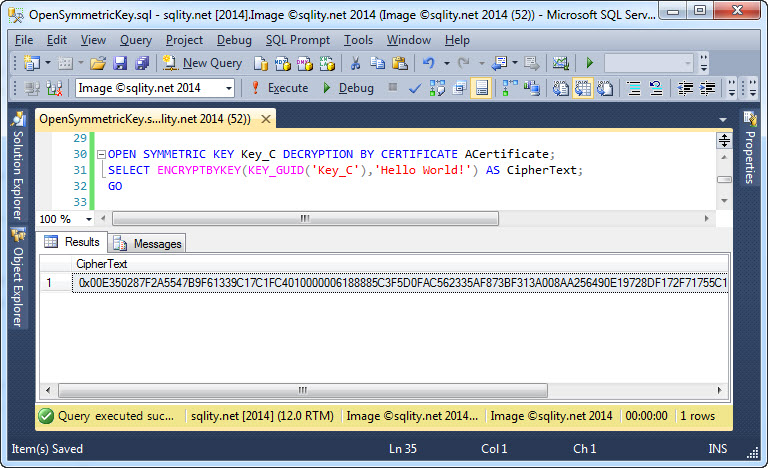
Don’t get caught in this nasty trap that will cause all your encrypted data to be wiped out. Discover how to use the OPEN SYMMETRIC KEY statement correctly to protect yourself (and your data) from this ugly surprise.
-
The sys.dm_db_database_page_allocations DMF
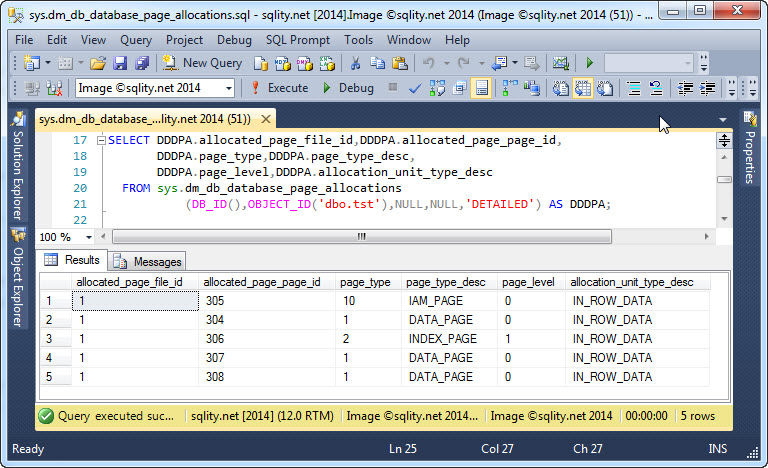
Are you looking for an alternative to DBCC IND? Read on to see how the new sys.dm_db_database_page_allocations DMF can be used to return all pages for a particular table (or even all tables in a database).
-
Security Blues [T-SQL Tuesday #56 – Assumptions]

When it comes to security related investments, we often make excuses why we should not invest now. But think about the impact a random breach can have., not only on you but on your clients, the very people that trusted you.
-
HASHBYTES: How to Calculate a Cryptographic Hash in T-SQL
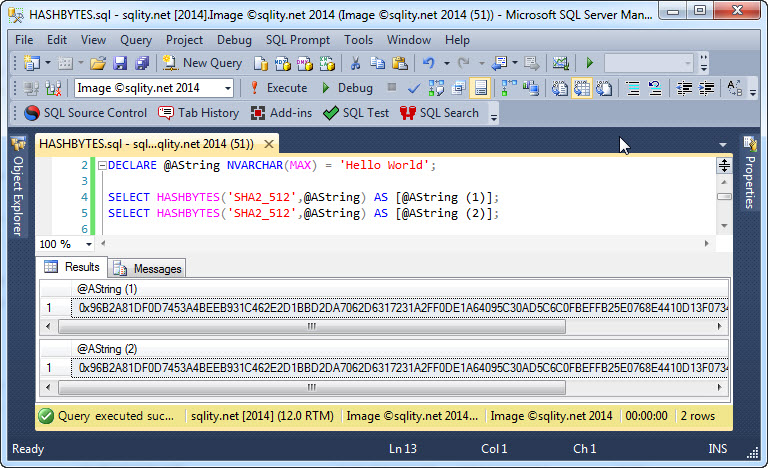
The HASHBYTES function provides a simple way to calculate cryptographic hash values in T-SQL. Read on to learn how to use this function and discover its two limitations.
-
Intermediate Index Pages in SQL Server
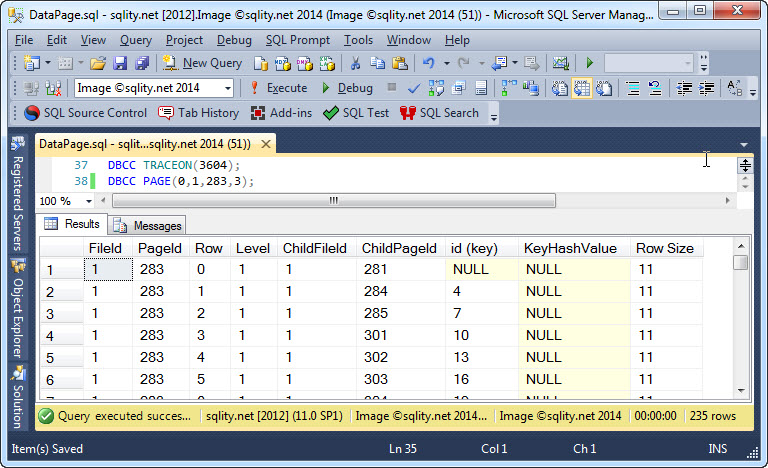
SQL Server stores indexes in B+ Tree format on disk. Each node is represented by a SQL Server page. The actual rows are stored in data pages while the index structure resides in intermediate index pages. Read on to find out more.
-
Hash Algorithms – How does SQL Server store Passwords?

How does SQL Server store its own passwords? Discover which hashing algorithm is used and how you can calculate your own password hash value in T-SQL.
-
Auditing SQL Server Password Strength using PWDCOMPARE
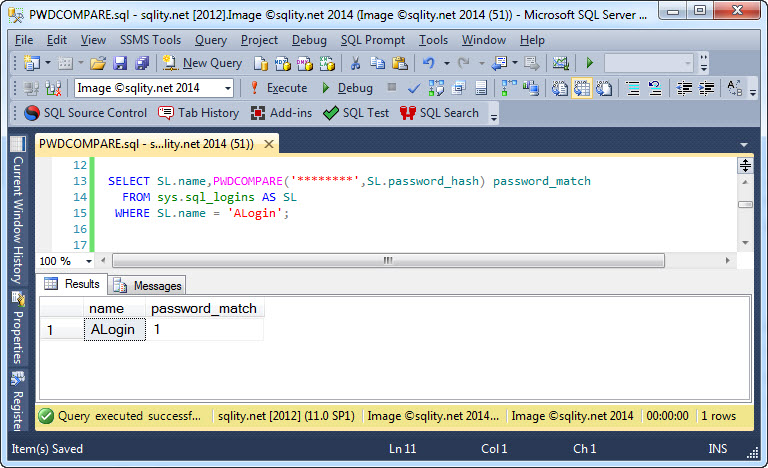
SQL Server stores passwords as salted hash values, preventing us from directly checking or enforcing their strength. However, using PWDCOMPARE we can try to crack them to identify weak ones.
-
Where are my Rows? – Using the %%physloc%% Virtual Column
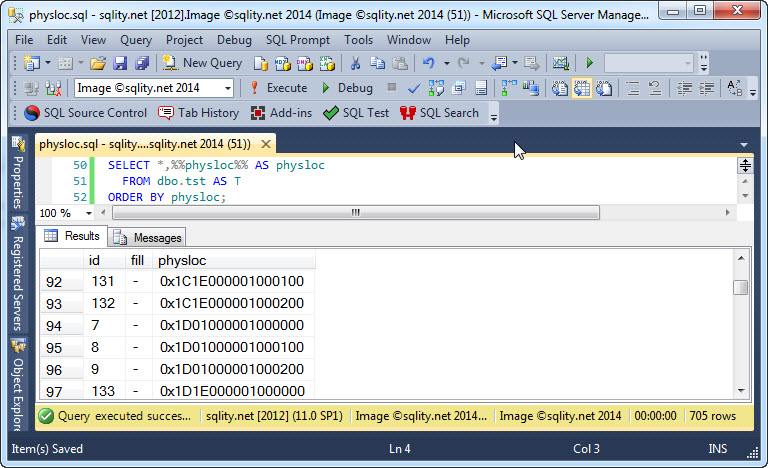
Sometimes it is helpful to know on which page exactly SQL Server has stored a particular row. You can use the undocumented %%physloc%% virtual column, together with its supporting functions sys.fn_PhysLocFormatter and sys.fn_PhysLocCracker, to find out.











