Blog
-
Creating an Asymmetric Key using a Strong Name File
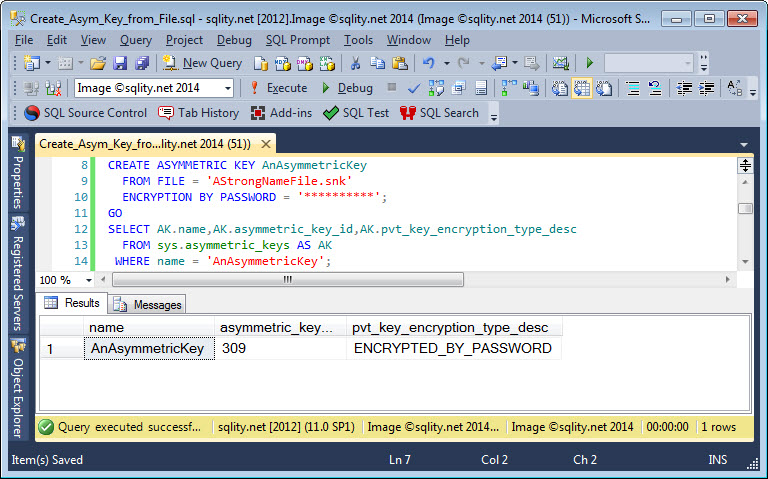
.NET Strong name files are built to hold a single asymmetric key pair. Read on to discover how to generate SQL Server asymmetric keys form strong name files.
-
The Secret of the Database Boot Page
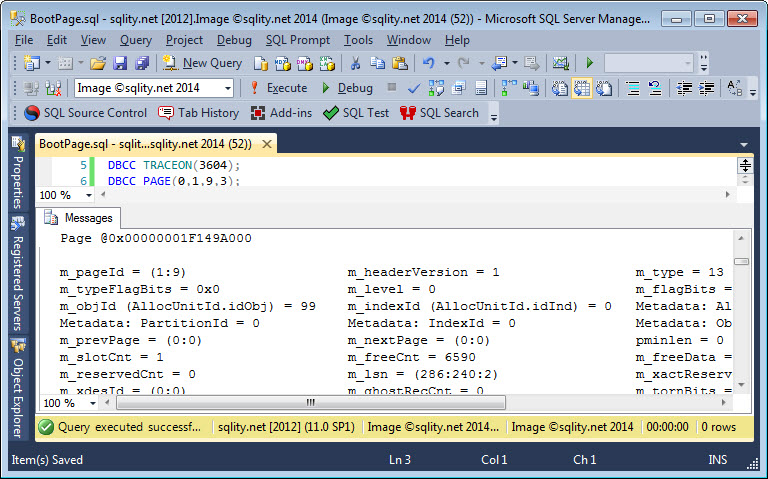
The database boot page contains database settings and configuration values. Read on to discover where to find this page and how to interpret its content.
[more…] -
The sys.asymmetric_keys Catalog View
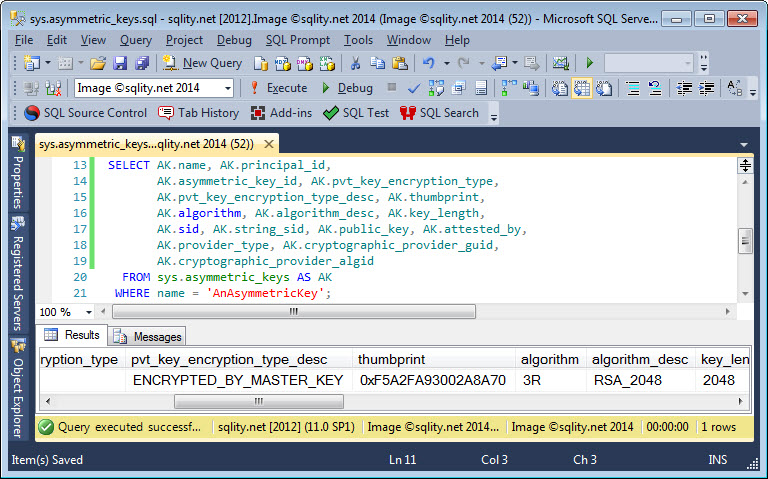
The sys.asymmetric_keys catalog view is a one-stop shop to get information about the asymmetric keys in the current database. Read on to discover how to use it.
-
CREATE ASYMMETRIC KEY – How to Generate an Asymmetric Key
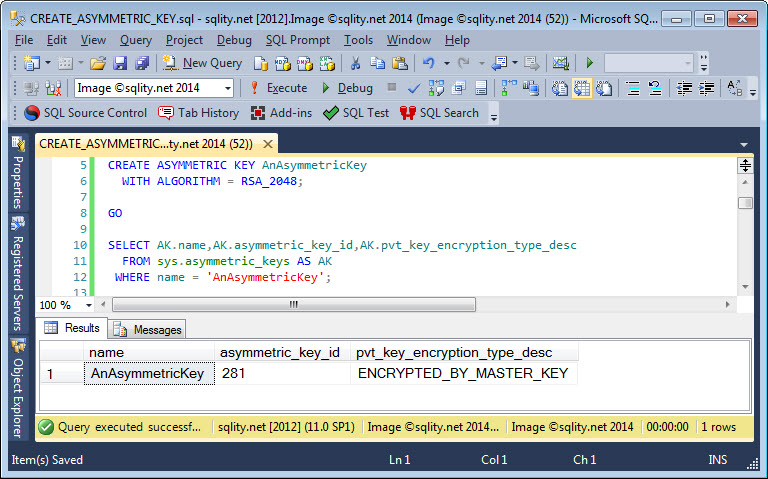
What is the difference between certificates and asymmetric keys in SQL Server and how do you generate asymmetric keys in T-SQL? Read on to get all the details.
-
DBCC FILEHEADER: Reading the File Header Page
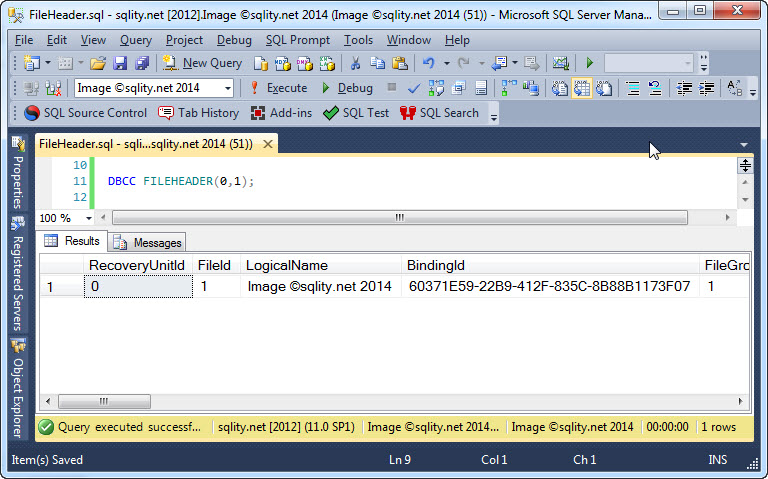
Every SQL Server database file has a dedicated file header page. Read on to discover how to use DBCC FILEHEADER to explore the header of your database files and learn about the one property of file header pages that might just affect your backup and restore strategy.
-
CERTPRIVATEKEY: Scripting the Private Key of a Certificate
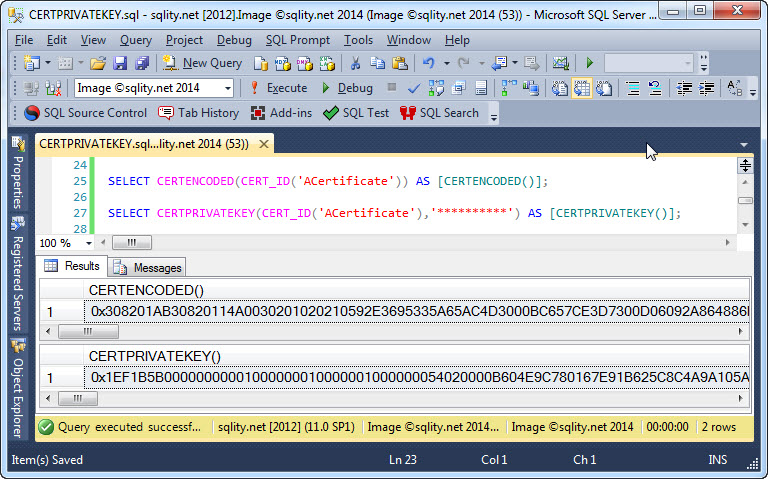
Find out how to convert the private key of a SQL Server certificate into a varbinary value using the built-in CERTPRIVATEKEY function.
-
CERTENCODED: How to Script your Certificates
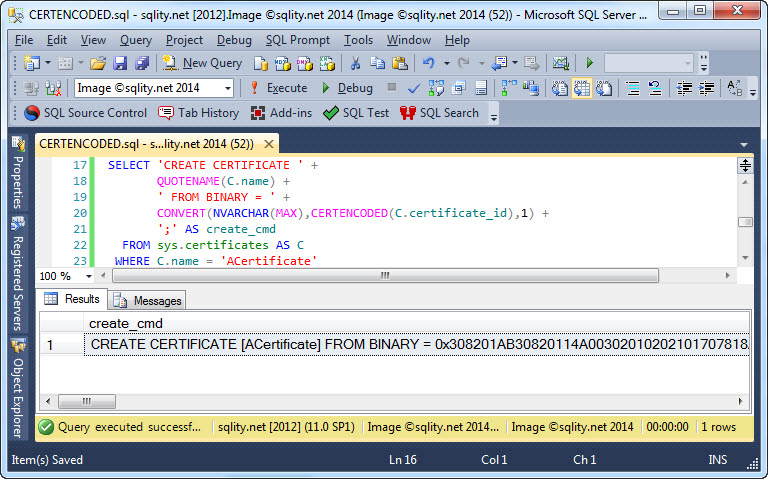
The ability to copy certificates from one database to another is often an important requirement in SQL Server security management. Read on to learn how to do just that effectively.
-
Bulk Changed Map (BCM): The Minimally Logged Advantage
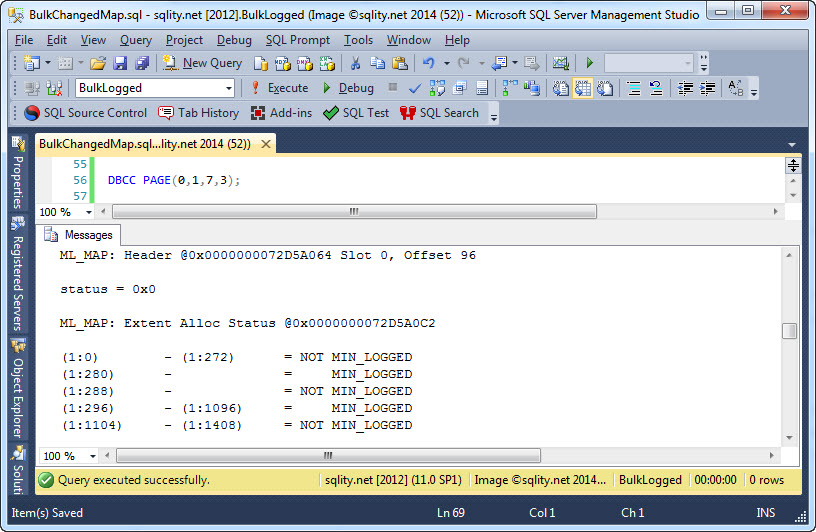
The Bulk-Logged recovery mode can provide a performance gain for your database. Check out how SQL Server uses the Bulk Changed Map to make this possible.
-
CERTPROPERTY – Digging Deeper into SQL Server Certificates
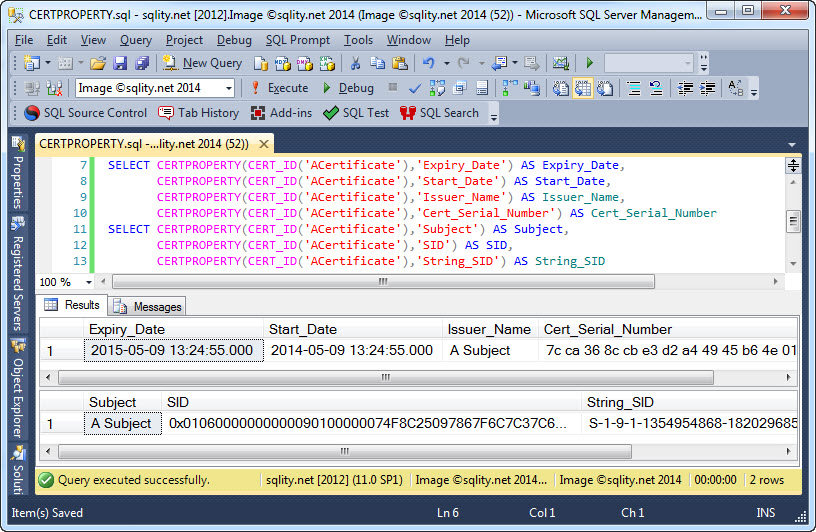
Discover how to read the properties of a specific SQL Server certificate using its certificate_id and the built-in CERTPROPERTY function.
-
How to Drop a Certificate Conditionally with CERT_ID
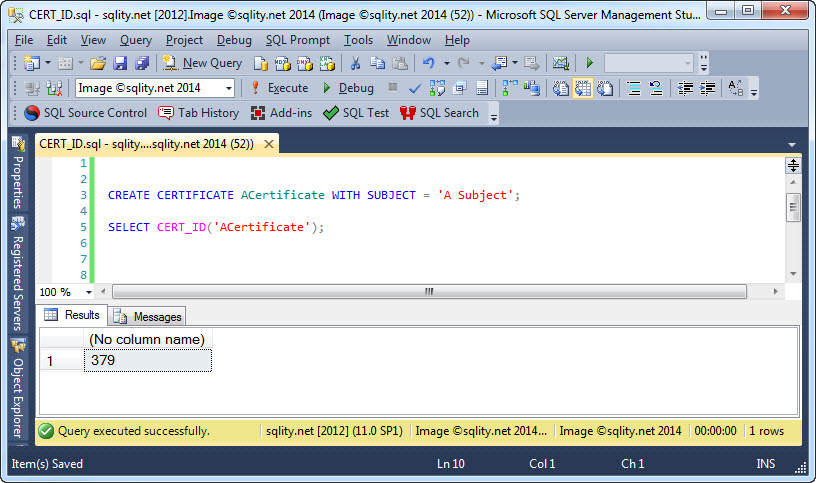
Discover how CERT_ID can be used to conditionally execute statements (like a drop or create) based on the existence of a specific certificate, since it returns a noon-NULL value only if the certificate exists.












