Blog
-
The SQL Server Encryption Hierarchy
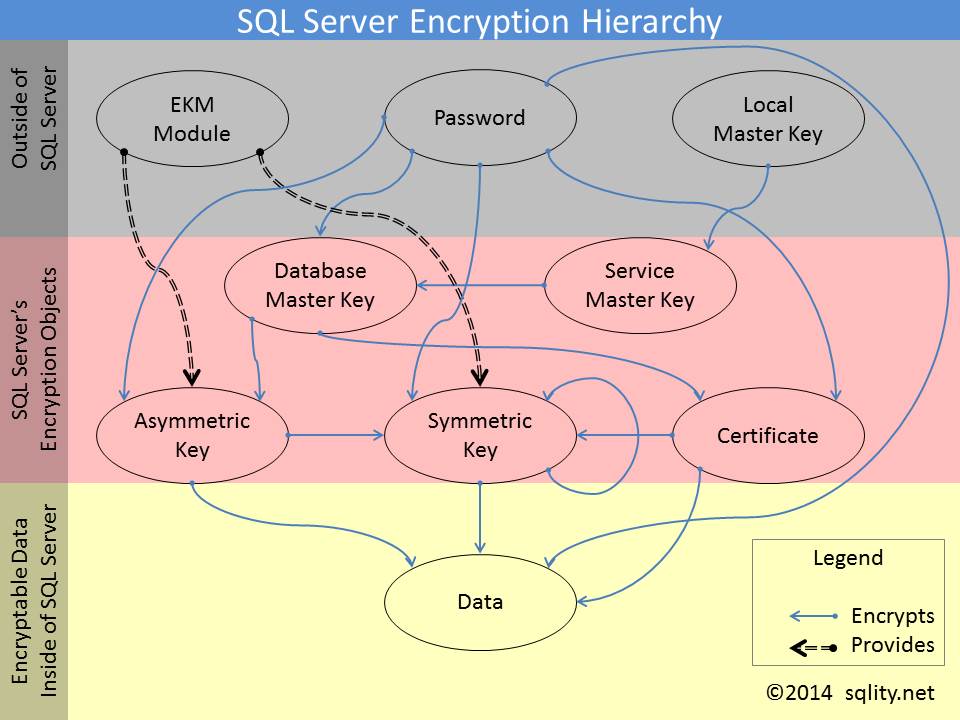
Discover how in SQL Server the different encryption keys can build a complex encryption hierarchy in which one key protects the next.
-
Auto Fix Orphaned Users
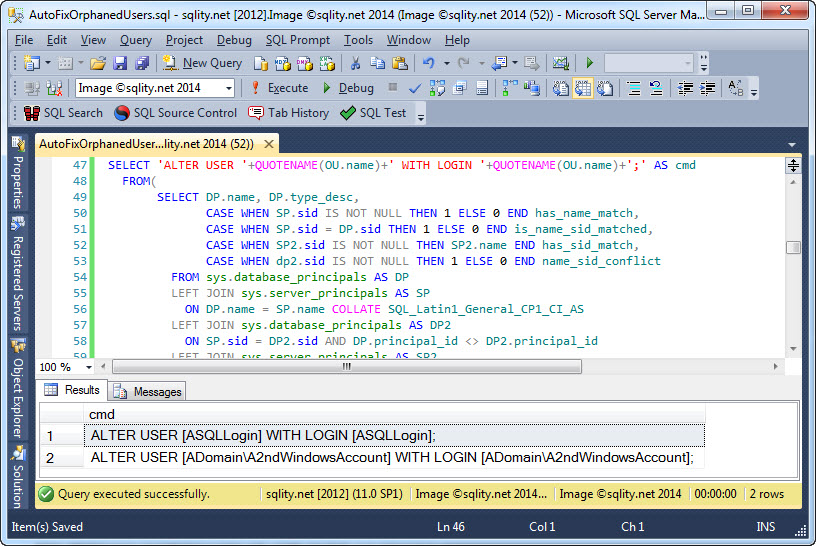
To auto fix orphaned users safely is a surprisingly complex task. But, as demonstrated in this article, it is possible if you follow a handful of rules.
-
The Global Allocation Map (GAM)
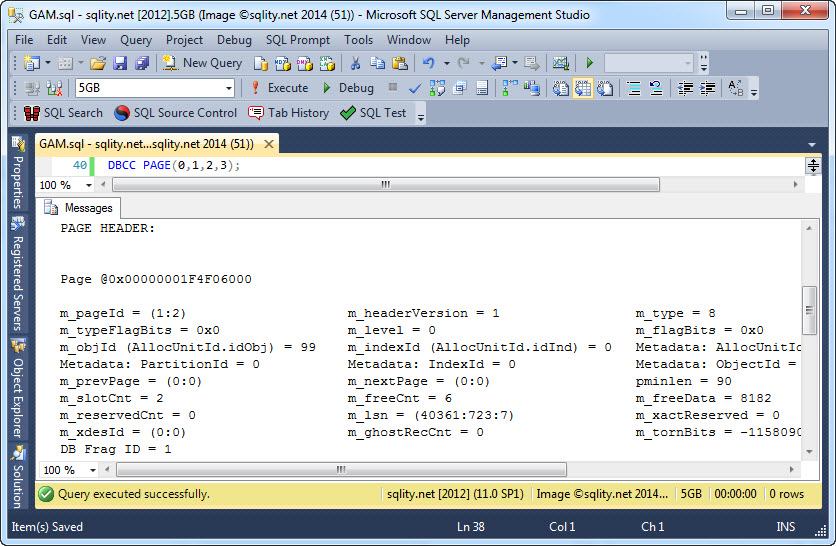
SQL Server uses the Global Allocation Map (GAM) to catalog if an extent is allocated or not. In a 7988-byte bitmap each extent is associated with a single bit to convey that information. Read on to get all the details.
-
Scripting All Logins on a SQL Server Instance
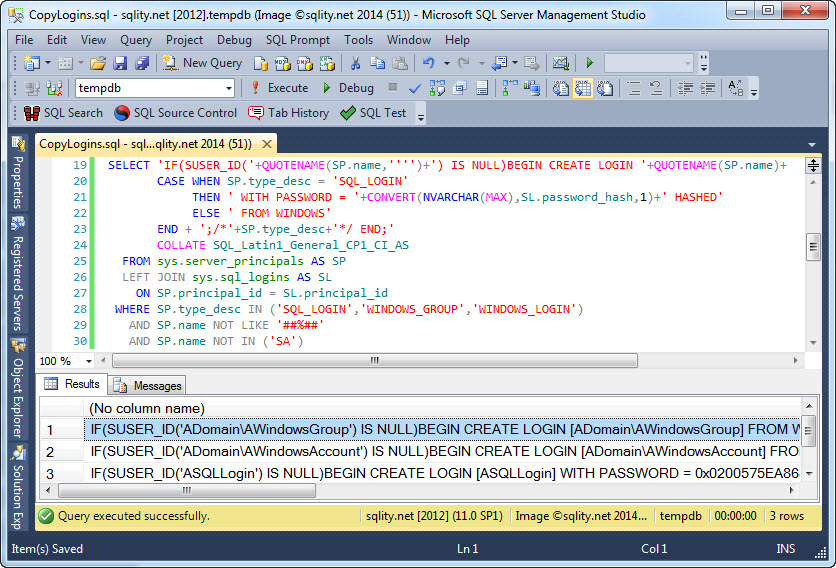
Scripting all logins on a SQL Server instance can be helpful e.g. when setting up a test or development environment. Read on to see an example query for just this purpose.
-
How to Re-Create a Login with only a Hashed Password

To re-create a login on a different SQL Server instance while preserving the password you can use the CREATE LOGIN statement with the hashed password. Read on for a detailed explanation.
-
How to Fix Orphaned Users in SQL Server
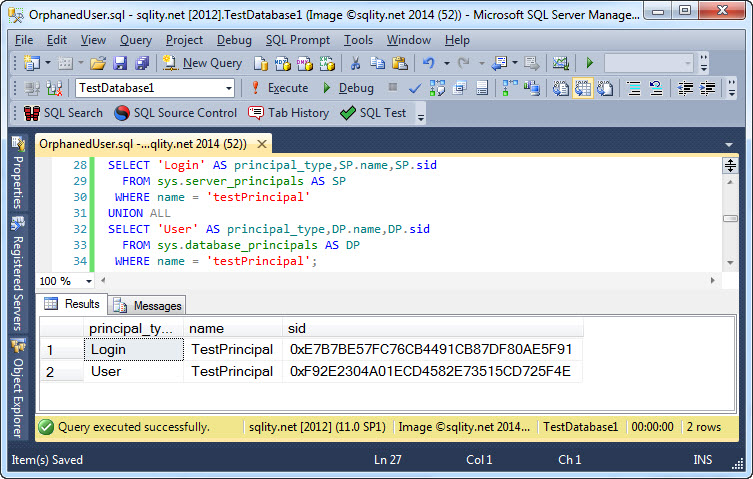
To access a database in SQL Server, a login needs to have an associated user in that database. Read on to see how that association is implemented and what you need to do to repair it if it breaks.
-
The GAM Interval and GAM Extents

What is a GAM extent in SQL Server? What is a GAM Interval and how big is it really? Read on now to get the answers to these questions and see why a GAM interval is not 64000 extents.
-
LOGINPROPERTY – Getting to know your SQL Logins even more

LOGINPROPERTY is a SQL Server catalog function that can be used to query a total of twelve properties for SQL Logins not even revealed by the sys.sql_logins catalog view. Read on to find out how to use LOGINPROPERTY and which properties it can return.
-
sys.sql_logins – Getting to know your SQL Logins

The sys.sql_logins catalog view can be used to retrieve additional information on SQL Logins that is not included in the sys.server_principals catalog view. Read on to find out what additional information is revealed by this catalog view.
-
How to Change a SQL Login’s Password

ALTER LOGIN can be used to change the password of a SQL Login. Read on to see the required permissions and what you need to do to change your own password.










