Tag: Certificates
-
Debunking Symmetric Key Recreate-Ability
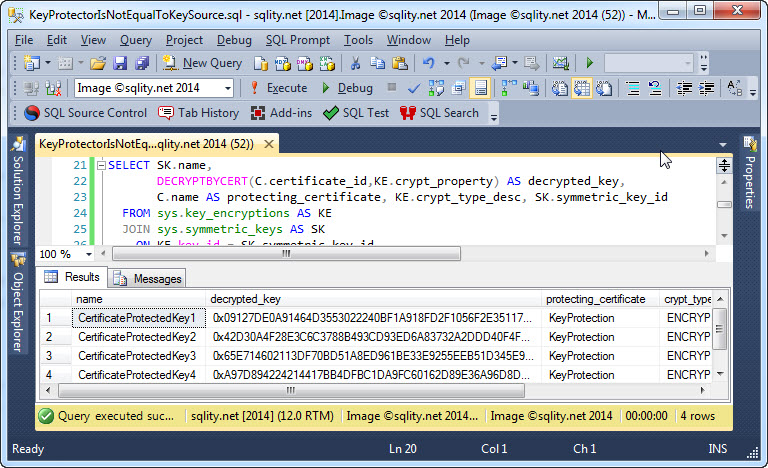
Do you think you can recreate a symmetric key that is protected by a certificate, by just using that same certificate? You might be in for a big surprise…
-
OPEN SYMMETRIC KEY – Avoid the NULL Ciphertext Trap
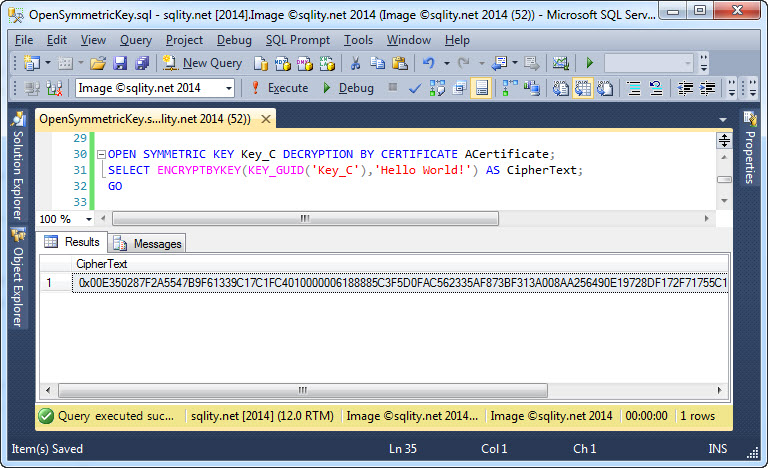
Don’t get caught in this nasty trap that will cause all your encrypted data to be wiped out. Discover how to use the OPEN SYMMETRIC KEY statement correctly to protect yourself (and your data) from this ugly surprise.
-
CREATE ASYMMETRIC KEY – How to Generate an Asymmetric Key
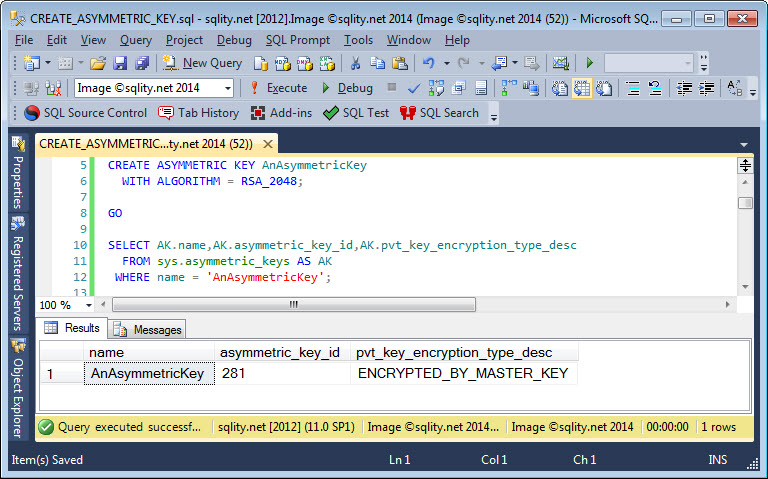
What is the difference between certificates and asymmetric keys in SQL Server and how do you generate asymmetric keys in T-SQL? Read on to get all the details.
-
CERTPRIVATEKEY: Scripting the Private Key of a Certificate
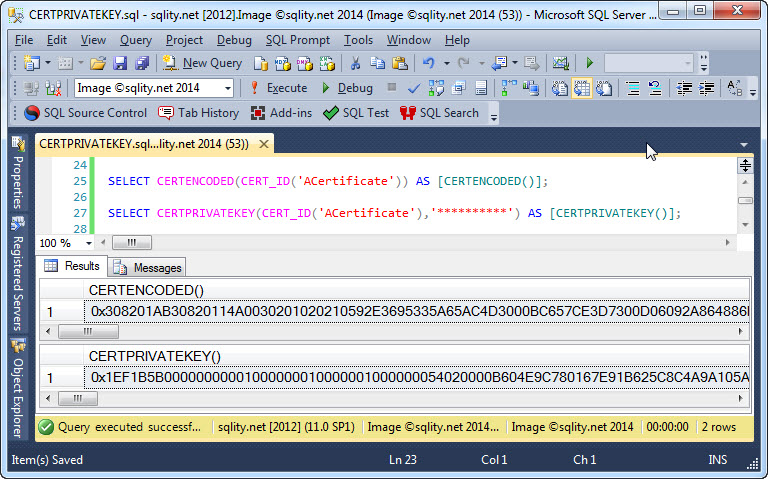
Find out how to convert the private key of a SQL Server certificate into a varbinary value using the built-in CERTPRIVATEKEY function.
-
CERTENCODED: How to Script your Certificates
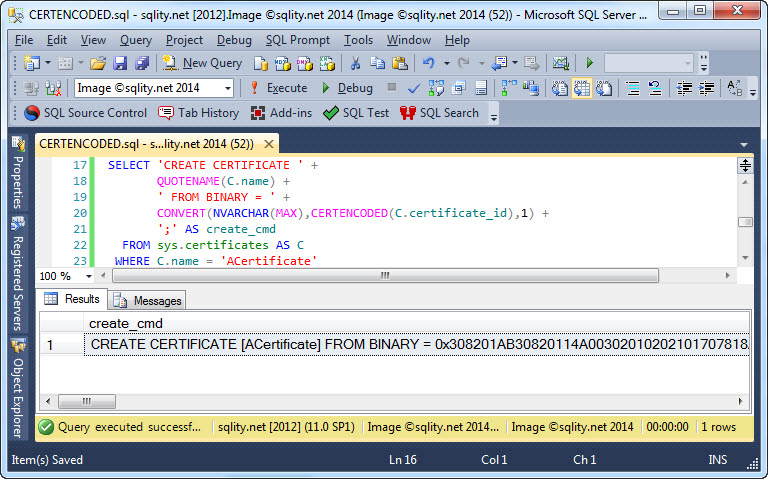
The ability to copy certificates from one database to another is often an important requirement in SQL Server security management. Read on to learn how to do just that effectively.












