Tag: Certificates
-
CREATE CERTIFICATE – How to create a Self-Signed Certificate in SQL Server
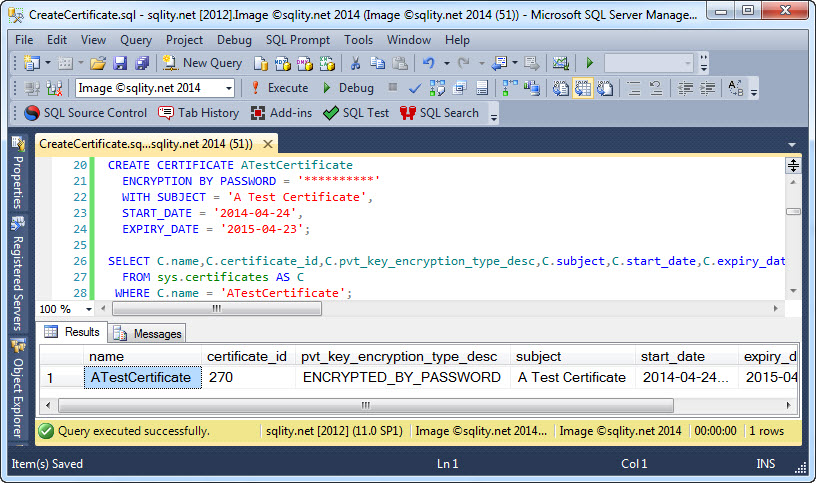
Discover how the CREATE CERTIFICATE T-SQL statement can be used to create a self-signed certificate, and what your options are to protect its private key.
-
The SQL Server Encryption Hierarchy
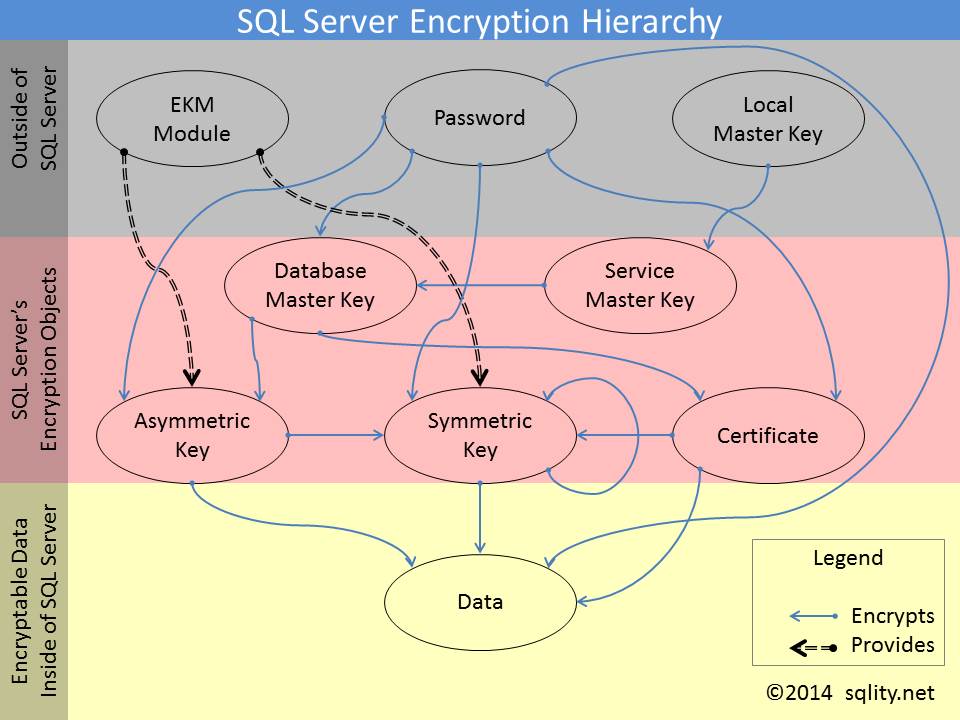
Discover how in SQL Server the different encryption keys can build a complex encryption hierarchy in which one key protects the next.
-
Certificates and the Chain of Trust

Certificates are containers for asymmetric encryption keys that can be used to establish a chain of trust between communicating parties. Read on to see how this works in practice.
-
SQL Server Database Users and the sys.database_principals catalog view

Database principals like the database user allow use to grant permissions on objects in a given database. Check out how to list users and find their linked logins.
-
SQL Server Logins and the sys.server_principals catalog view

SQL Server knows two types of security principals: The login or server principal and the database user or database principal. Read on to learn more about the server principal.












