Tag: security management
-
Common Database Vulnerabilities: Privilege Abuse

Privilege abuse comes in two forms: Abuse of excessive and of legitimate privileges. Discover how to protect your environment from this vulnerability.
-
Auditing SQL Server Password Strength using PWDCOMPARE
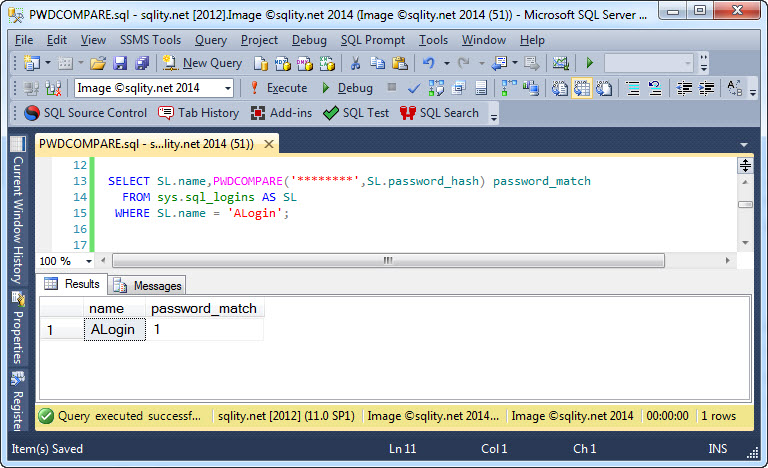
SQL Server stores passwords as salted hash values, preventing us from directly checking or enforcing their strength. However, using PWDCOMPARE we can try to crack them to identify weak ones.
-
The SQL Server Encryption Hierarchy
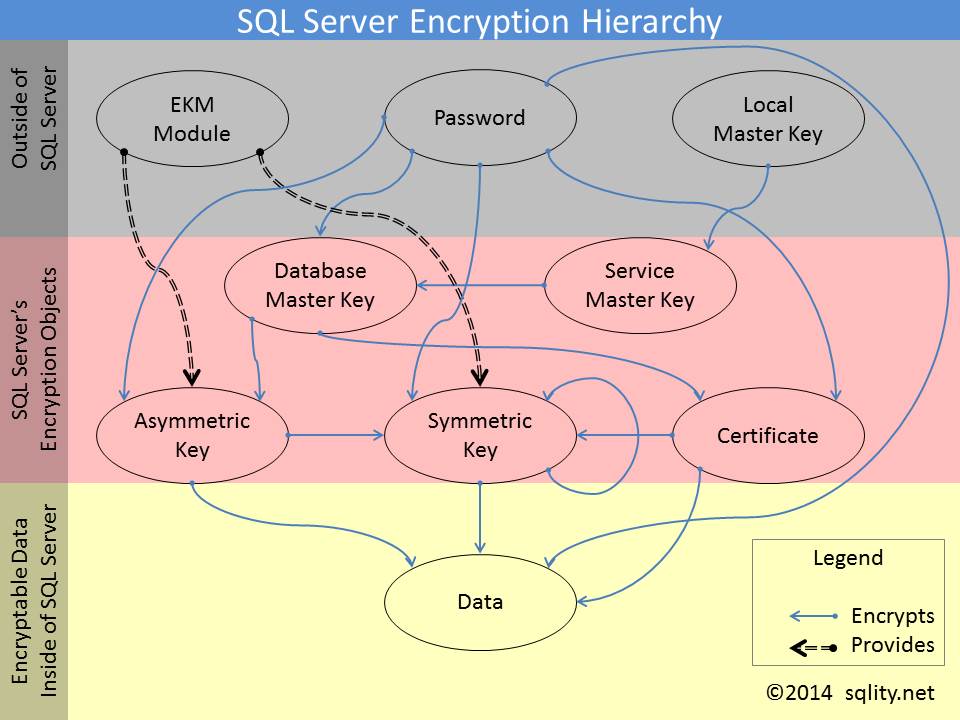
Discover how in SQL Server the different encryption keys can build a complex encryption hierarchy in which one key protects the next.
-
Auto Fix Orphaned Users
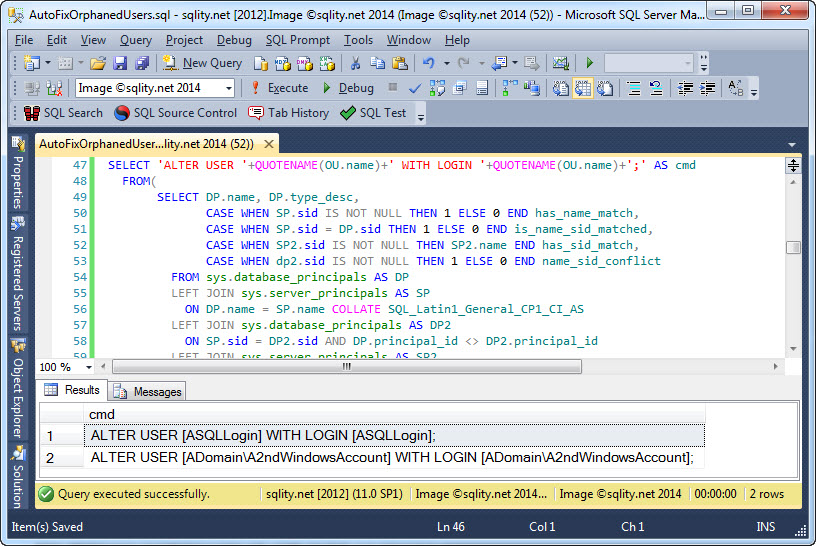
To auto fix orphaned users safely is a surprisingly complex task. But, as demonstrated in this article, it is possible if you follow a handful of rules.
-
Scripting All Logins on a SQL Server Instance
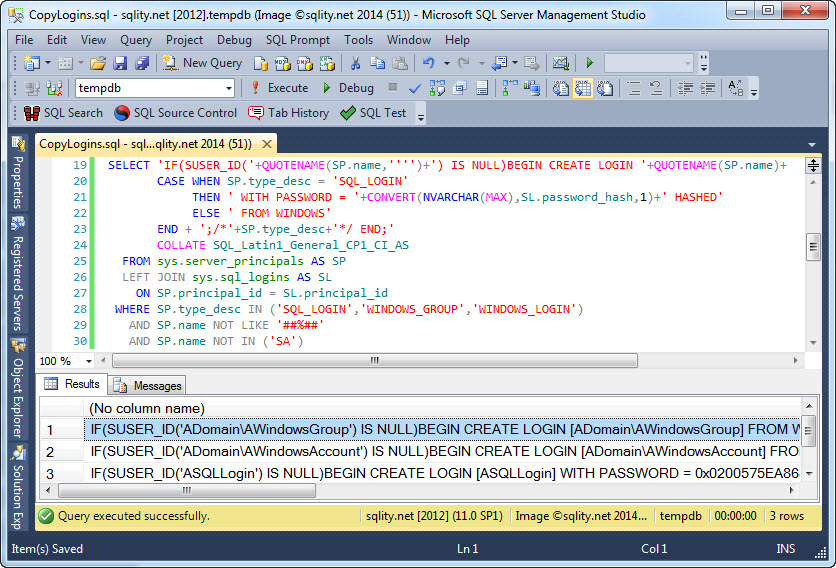
Scripting all logins on a SQL Server instance can be helpful e.g. when setting up a test or development environment. Read on to see an example query for just this purpose.












