Category: General
-
How to Create a Service Master Key in SQL Server
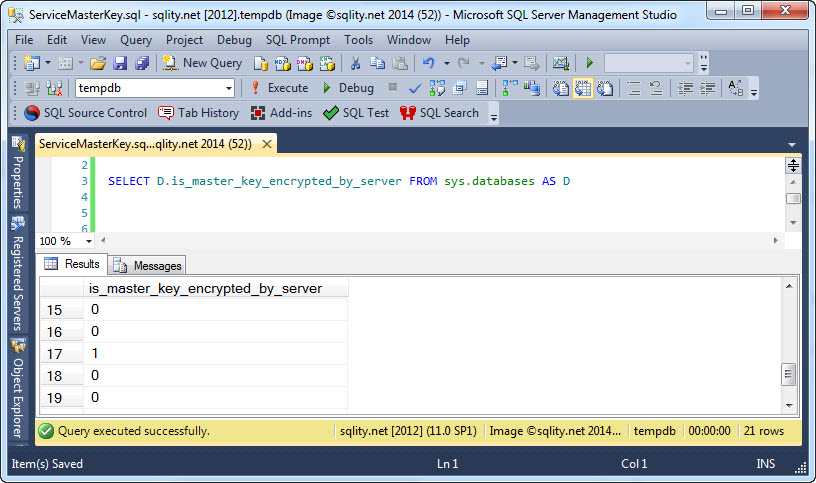
Discover how the service master key is created, what it protects and how it is protected itself, and learn about the two important security implications that arise from the protection mechanism used.
-
The Shared Global Allocation Map (SGAM)
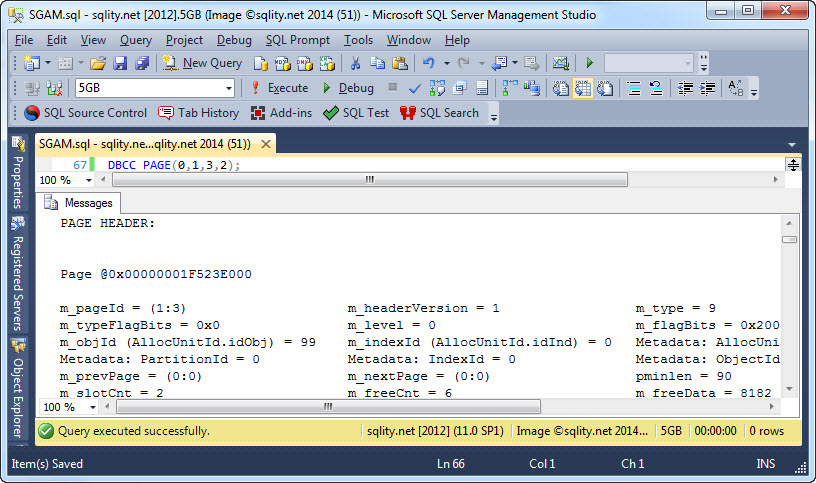
Discover how SQL Server tracks mixed extents containing free pages using a Shared Global Allocation Map made up of one SGAM page per GAM Interval.
-
How to Pick a Good Password

Do you know why you care about picking a good password and why reusing a password is a bad idea, even if you think your life is boring to a would-be hacker. Read on to discover how hackers get a hold of long lists of usernames and passwords and that a hack on a random page you might have used once can be a real threat to your online life.
-
The SQL Server Encryption Hierarchy
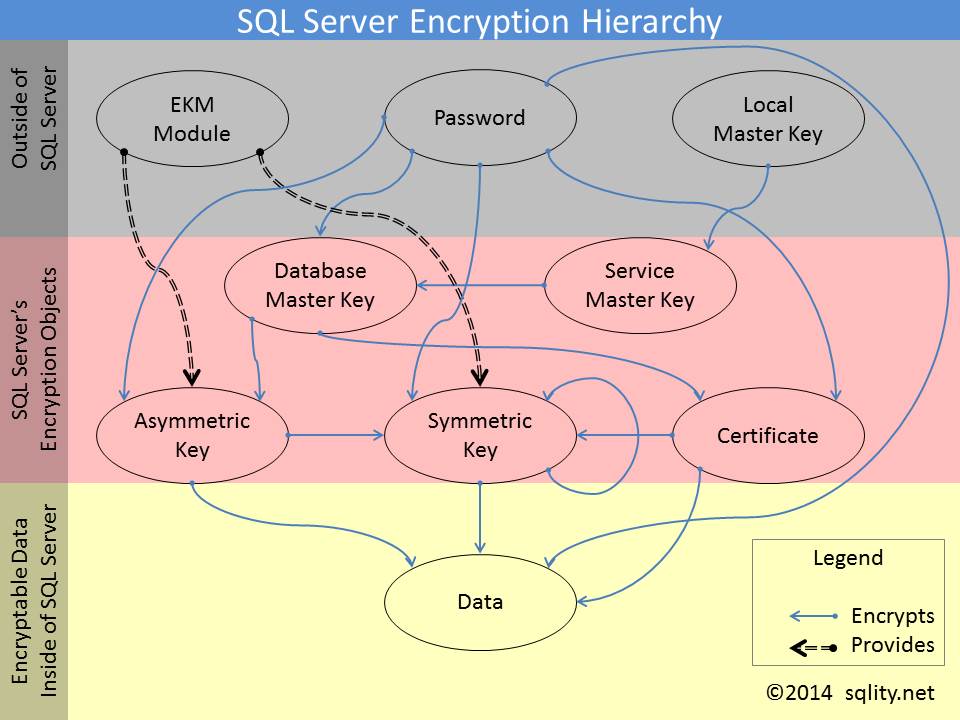
Discover how in SQL Server the different encryption keys can build a complex encryption hierarchy in which one key protects the next.
-
Auto Fix Orphaned Users
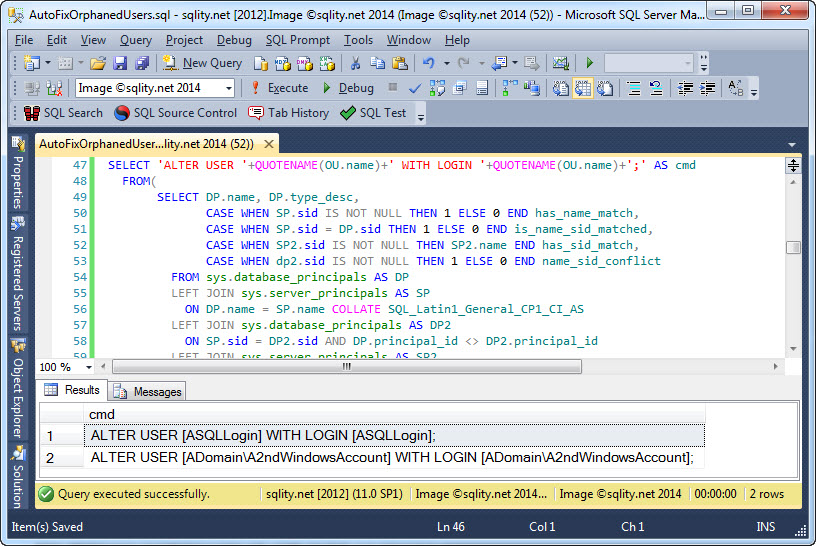
To auto fix orphaned users safely is a surprisingly complex task. But, as demonstrated in this article, it is possible if you follow a handful of rules.












