Category: General
-
The Cost of a Data Breach

Can you afford the immediate as well as the hidden cost of a data breach in your company? Find out now.
-
Common Database Vulnerabilities: Privilege Abuse

Privilege abuse comes in two forms: Abuse of excessive and of legitimate privileges. Discover how to protect your environment from this vulnerability.
-
Hey, where is my BLOB?
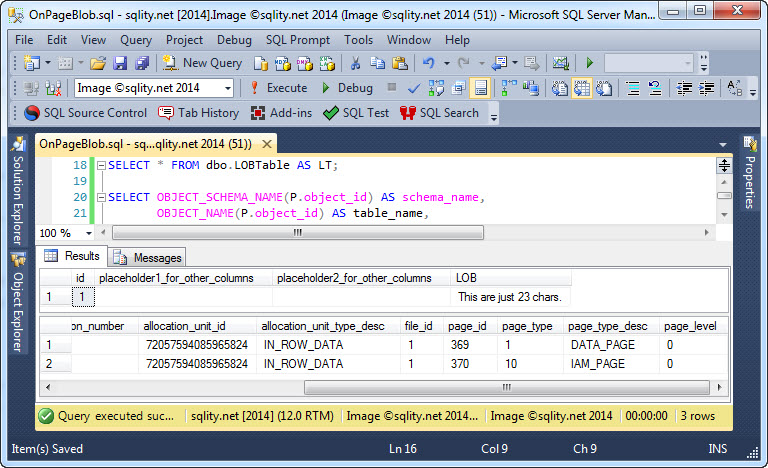
LOB values are not always stored in the special LOB_DATA allocation unit. But, where else could they be? Discover the well-kept secret of the Inline LOB.
-
How to Access Passphrase-Encrypted Data
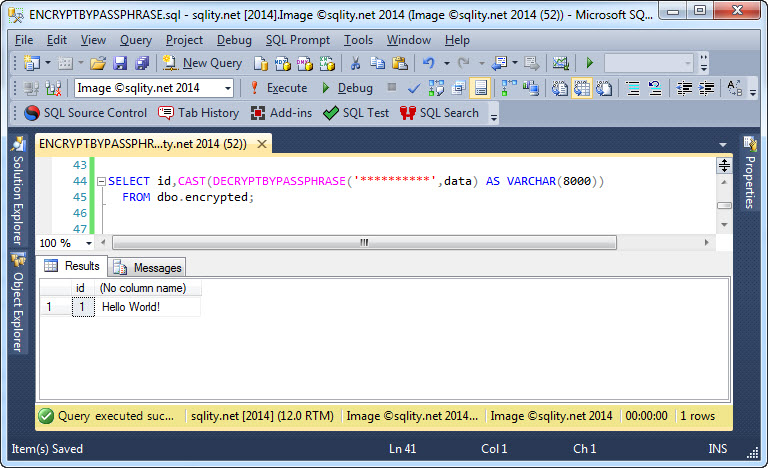
What do you need to do to decrypt data that was encrypted with ENCRYPTBYPASSPHRASE? Read on to see the DECRYPTBYPASSPHRASE function in action.
-
How to Encrypt a Column with a Passphrase
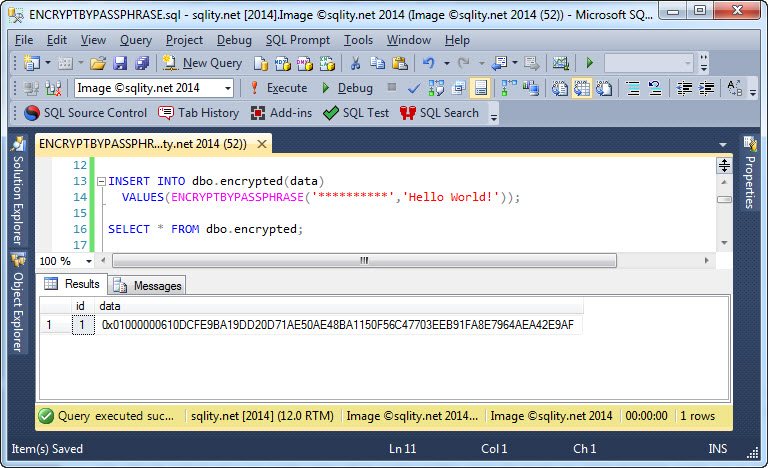
If you are searching for a quick and dirty way to encrypt data in SQL Server, the ENCRYPTBYPASSPHRASE function might be just what you are looking for.












