Category: General
-
How to Crack the Symmetric Keys in the Database Wide Open
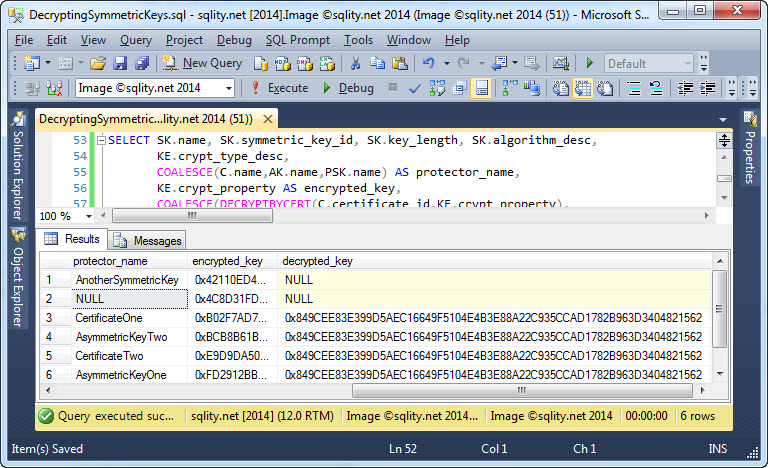
Did you always want to get to the root of symmetric key encryption in SQL Server and actually decrypt a protected symmetric key? In some circumstances this can actually be done. Find out how to do this now.
-
OPEN SYMMETRIC KEY – Avoid the NULL Ciphertext Trap
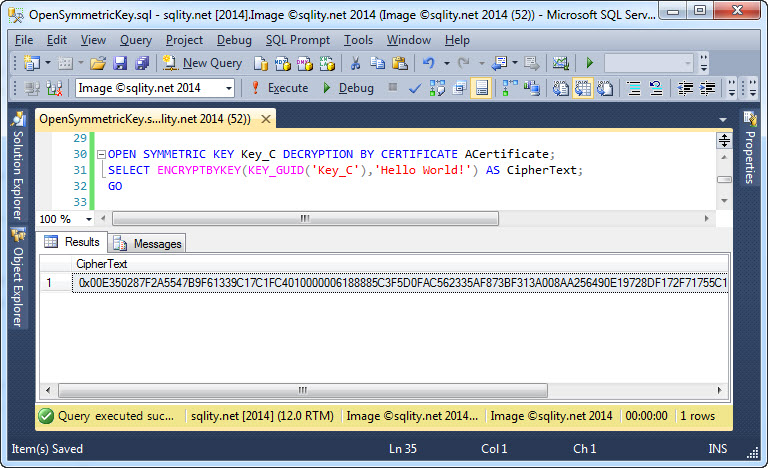
Don’t get caught in this nasty trap that will cause all your encrypted data to be wiped out. Discover how to use the OPEN SYMMETRIC KEY statement correctly to protect yourself (and your data) from this ugly surprise.
-
The sys.dm_db_database_page_allocations DMF
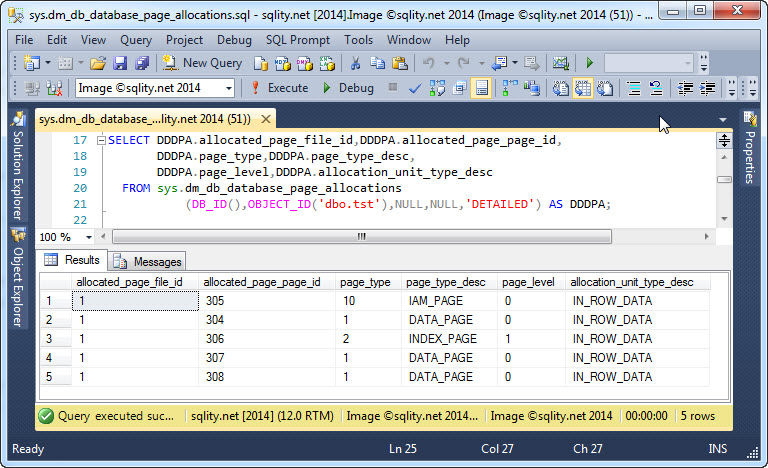
Are you looking for an alternative to DBCC IND? Read on to see how the new sys.dm_db_database_page_allocations DMF can be used to return all pages for a particular table (or even all tables in a database).
-
Security Blues [T-SQL Tuesday #56 – Assumptions]

When it comes to security related investments, we often make excuses why we should not invest now. But think about the impact a random breach can have., not only on you but on your clients, the very people that trusted you.
-
HASHBYTES: How to Calculate a Cryptographic Hash in T-SQL
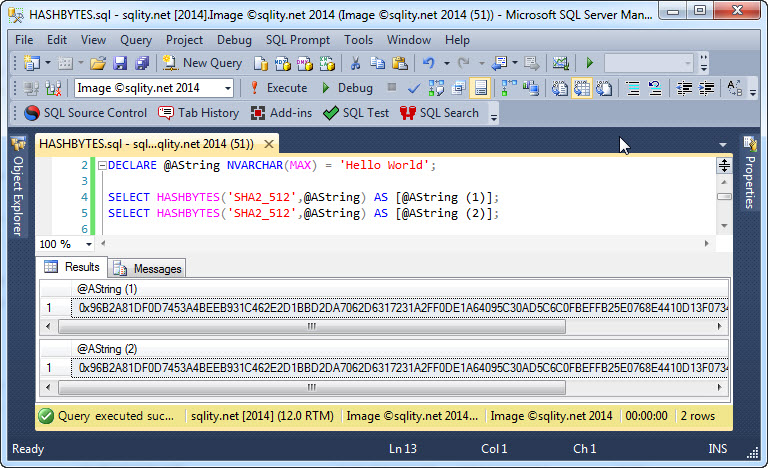
The HASHBYTES function provides a simple way to calculate cryptographic hash values in T-SQL. Read on to learn how to use this function and discover its two limitations.












