Blog
-
The sys.key_encryptions Catalog View
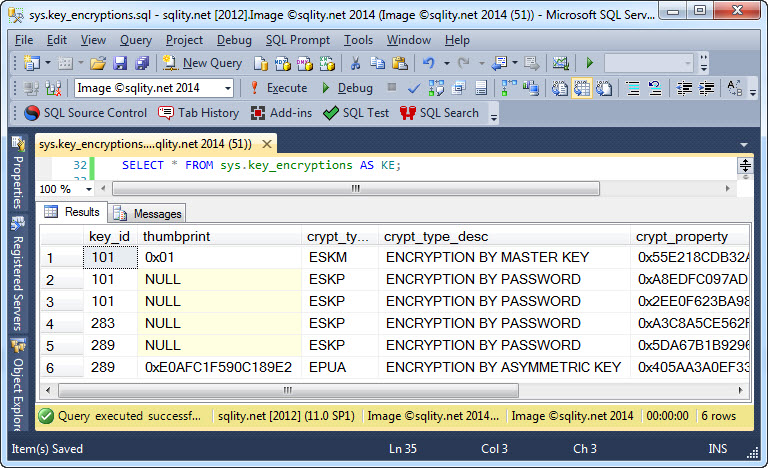
Do you have a symmetric key in a SQL Server database but forgot how it is encrypted? Discover how you can use the sys.key_encryptions catalog view to find out which protection mechanisms were used to encrypt the symmetric keys in the current database.
-
Five Reasons why You Need to Encrypt Your PHI

Are you a covered entity under the HIPAA rules and do you store PHI (Protected Health Information) in your database? Here are five reasons why you really should encrypt that data.
-
B+Trees – How SQL Server Indexes are Stored on Disk

How does SQL Server organize clustered and non-clustered indexes on disk? SQL server uses B+Trees. Read on to find out what B+Trees are and how they are implemented in SQL Server.
-
The sys.symmetric_keys Catalog View
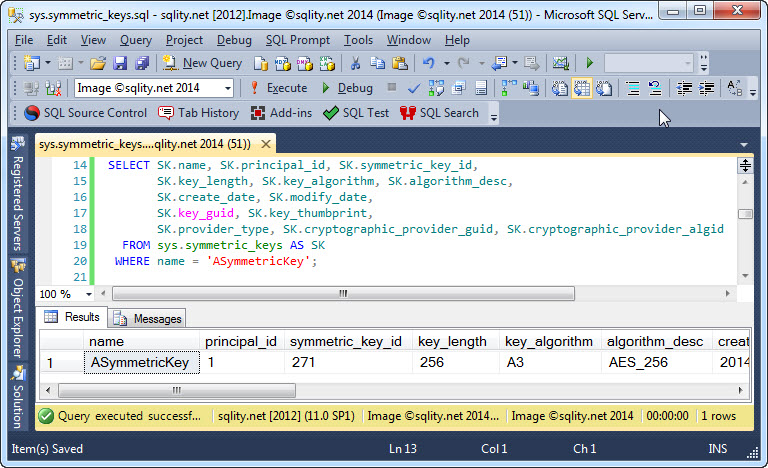
Where do you turn if you need information about the symmetric keys in the current database? Meet the sys.symmetric_keys catalog view and discover what types of information on symmetric keys it can provide.
-
How to Create a Symmetric Key
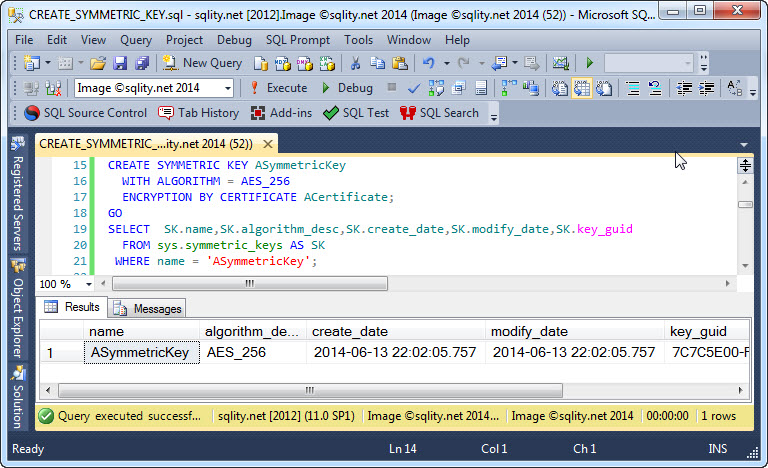
Encrypting large amounts of data in SQL Server should be done with symmetric key encryption. Discover how to create the necessary key for this encryption type.
-
The Server Configuration Page
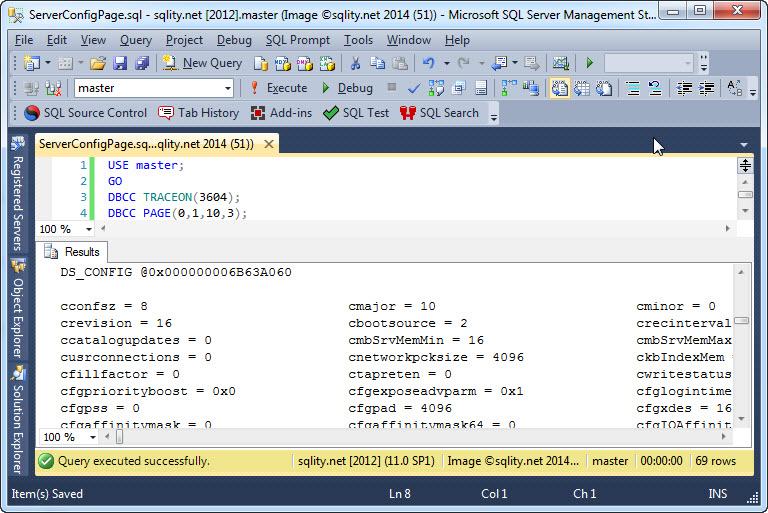
The Server Configuration Page is the place where SQL Server stores its configuration values (sp_configure). It is of a special page type that is found only once per SQL Server instance. Read on to get all the details.
-
How to Back Up the Database Master Key

The Database Master Key is often required to access any encrypted data in a SQL Server database. Therefore, it is important to always have a good backup of this important asset. Learn how to use the BACKUP MASTER KEY statement to backup this master key.
-
How to Back Up the Service Master Key

In SQL Server the Service Master Key is probably the most important encryption entity. Because of that, it needs to be protected and backed up. Read on to discover how to take a backup of this key encryption key.
-
Presentation Materials: Securing Multi-Database Applications

Abstract It is difficult enough to implement database security when dealing with only a single database. If multiple databases are involved, the task of providing a security model that follows industry best practices seems insurmountable. In this session, we will [more…]
-
The Missing BACKUP ASYMMETRIC KEY statement
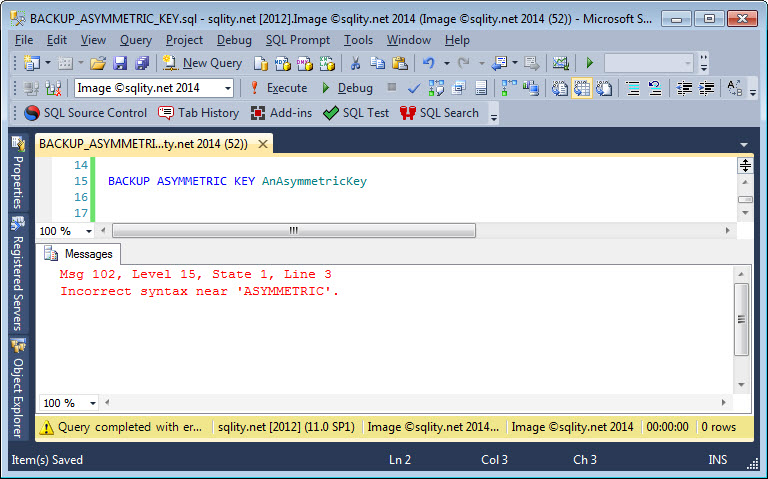
Is the BACKUP ASYMMETRIC KEY statement really missing from the T-SQL language? Read on to discover the truth and see if there are any viable alternatives.











