Tag: Cryptography
-
HASHBYTES: How to Calculate a Cryptographic Hash in T-SQL
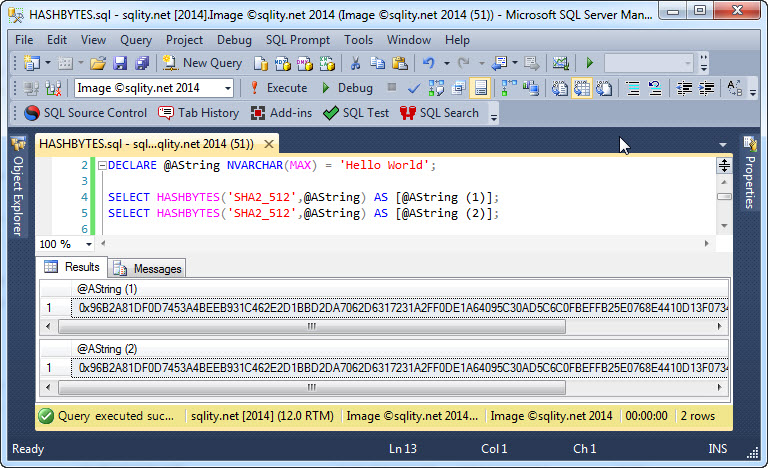
The HASHBYTES function provides a simple way to calculate cryptographic hash values in T-SQL. Read on to learn how to use this function and discover its two limitations.
-
The sys.key_encryptions Catalog View
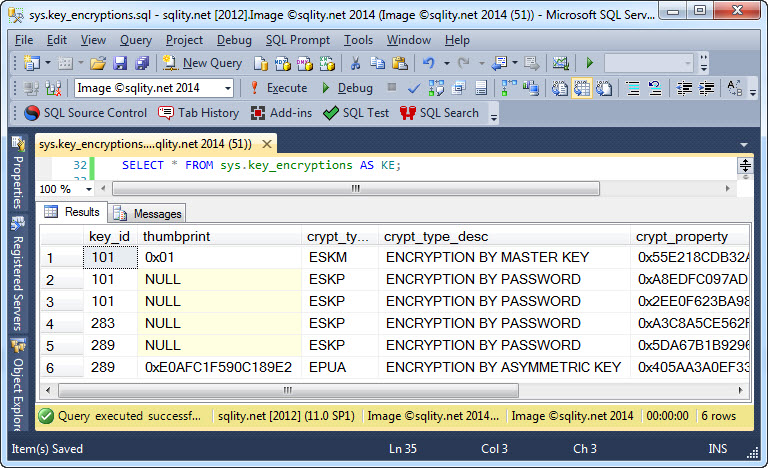
Do you have a symmetric key in a SQL Server database but forgot how it is encrypted? Discover how you can use the sys.key_encryptions catalog view to find out which protection mechanisms were used to encrypt the symmetric keys in the current database.
-
Five Reasons why You Need to Encrypt Your PHI

Are you a covered entity under the HIPAA rules and do you store PHI (Protected Health Information) in your database? Here are five reasons why you really should encrypt that data.
-
The sys.symmetric_keys Catalog View
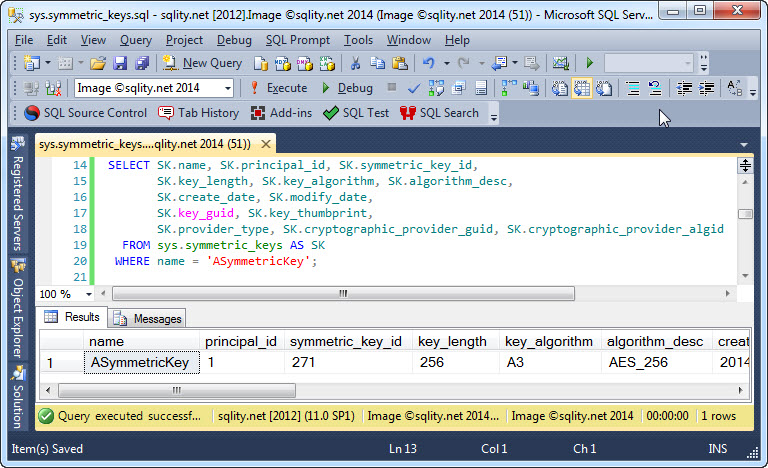
Where do you turn if you need information about the symmetric keys in the current database? Meet the sys.symmetric_keys catalog view and discover what types of information on symmetric keys it can provide.
-
How to Create a Symmetric Key
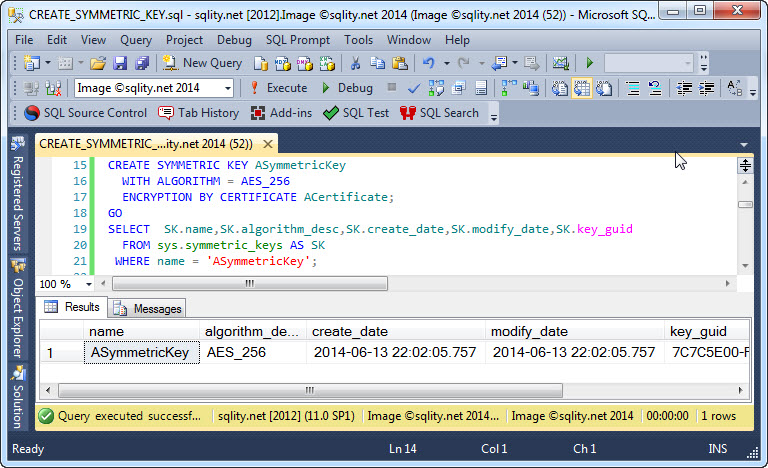
Encrypting large amounts of data in SQL Server should be done with symmetric key encryption. Discover how to create the necessary key for this encryption type.












