Category: Security
-
How to Script Database Permissions
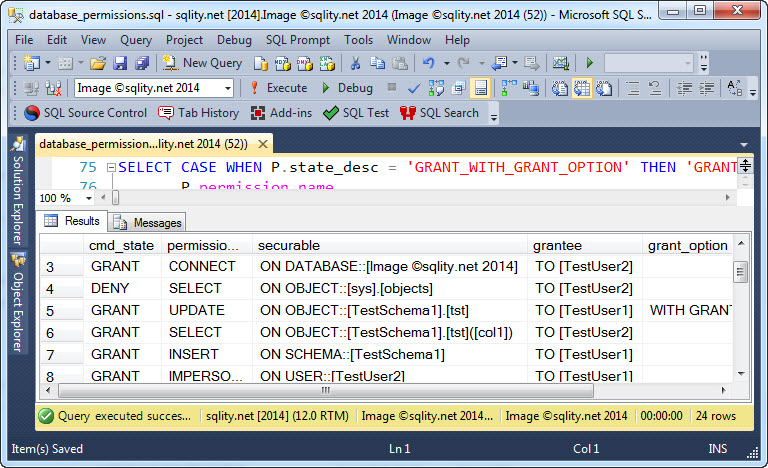
Scripting all permissions in a SQL Server database is not trivial. Discover how to generate the necessary statements yourself with this simple query. (Well, copy & paste of the query is simple…)
-
How to Crack the Symmetric Keys in the Database Wide Open
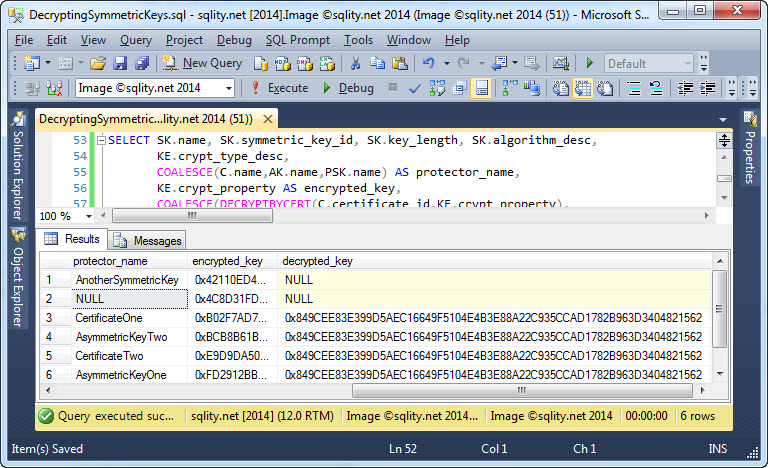
Did you always want to get to the root of symmetric key encryption in SQL Server and actually decrypt a protected symmetric key? In some circumstances this can actually be done. Find out how to do this now.
-
Auditing SQL Server Password Strength using PWDCOMPARE
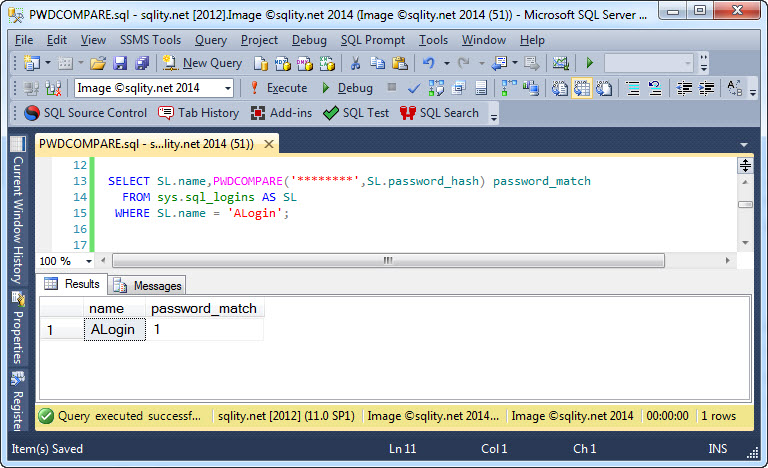
SQL Server stores passwords as salted hash values, preventing us from directly checking or enforcing their strength. However, using PWDCOMPARE we can try to crack them to identify weak ones.
-
The sys.key_encryptions Catalog View
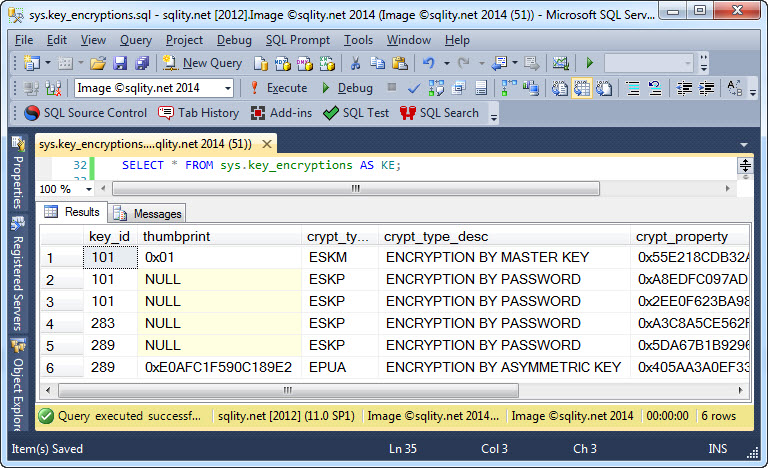
Do you have a symmetric key in a SQL Server database but forgot how it is encrypted? Discover how you can use the sys.key_encryptions catalog view to find out which protection mechanisms were used to encrypt the symmetric keys in the current database.
-
The sys.symmetric_keys Catalog View
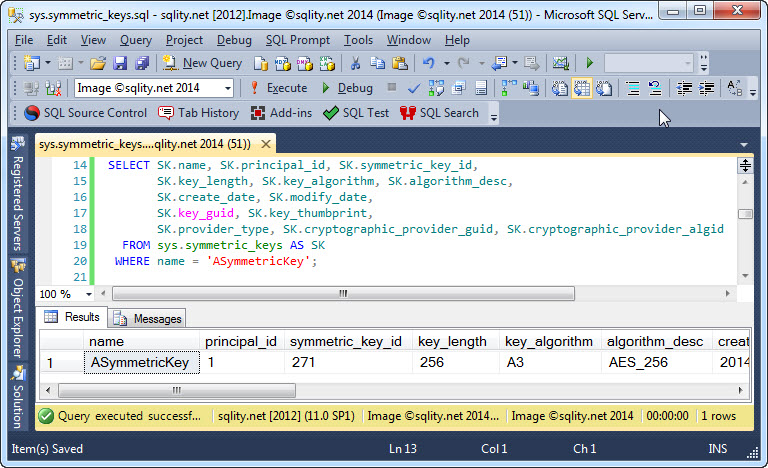
Where do you turn if you need information about the symmetric keys in the current database? Meet the sys.symmetric_keys catalog view and discover what types of information on symmetric keys it can provide.












